Introduction
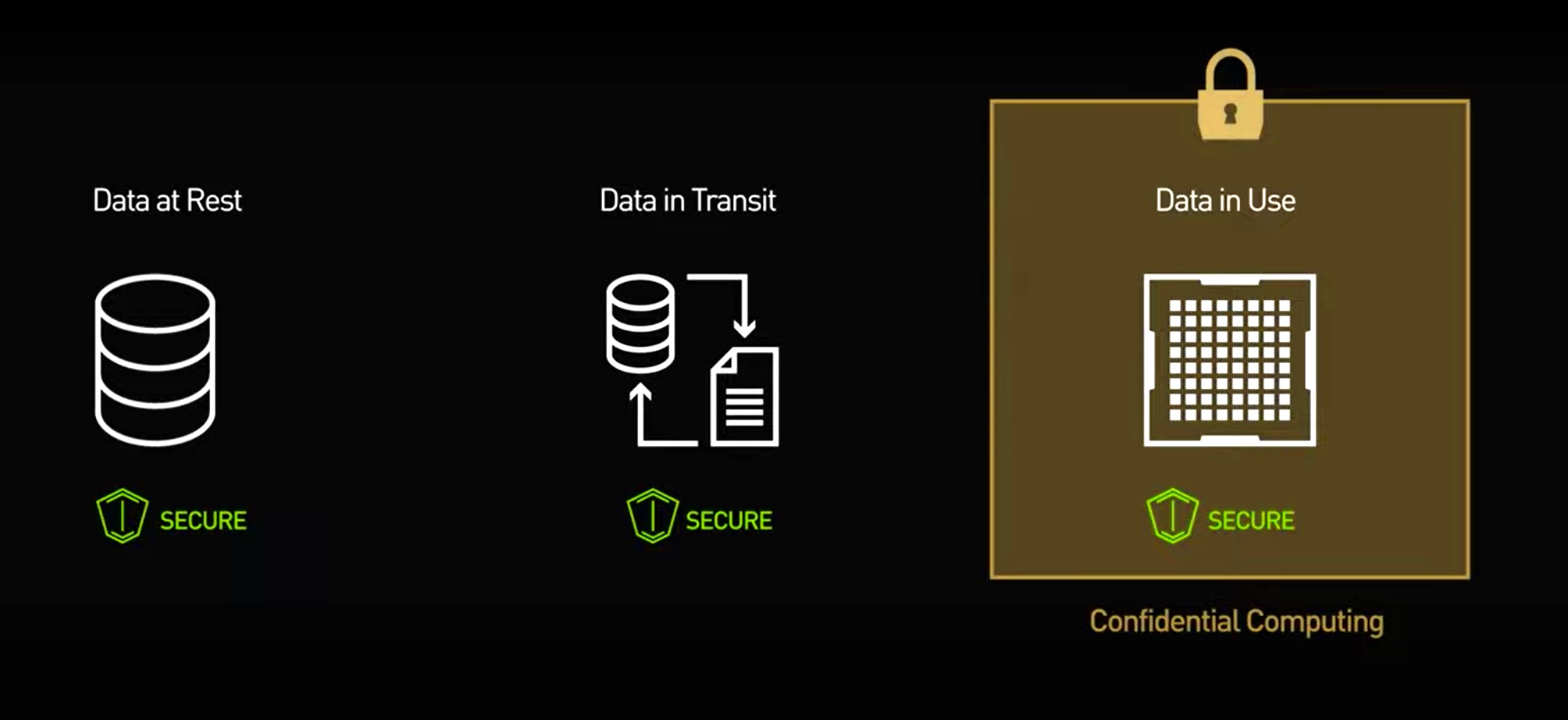
Confidential computing is a cloud computing technology that isolates sensitive data in a protected CPU enclave during processing. This helps ensure the integrity of the operating system you choose to run in your Confidential VM. Confidential Computing can unlock computing scenarios that have previously not been possible. Organizations will now be able to collaborate on sensitive and regulated data in the cloud, all while preserving confidentiality.
This was a mere definition, let's get a birds-eye view of how this thing even manifested in the real world.
Role of Trusted Execution Environment (TEE)
At a higher level, it's just a secure computing environment, but trusted means it provides certain properties. First, it must provide confidentiality in the confidentiality, integrity, and availability triad. Also, provides users with data confidentiality, data integrity, and code integrity. Various mechanisms like trust zone and arm processors have this capacity to do it.
Recently, Intel Software guard extensions (SGX) have come to the scene to provide this capability to general-purpose user-level software.
SGX (Software Guard Extension)
It helps protect data in use via unique application isolation technology. Protect selected code and data from modification using hardened enclaves with Intel SGX. So, the SGX provides two main categories of protection because it uses well-defined instructions.
- It can separate what code is executing and which data within this trusted environment. It provides a very strong separation.
- It provides memory protection capabilities as most data and code is stored in memory. Specifically, it provides memory encryption and data integrity as well as anti-replay capabilities.
Intel has a similar VM-based approach called TDX (Trusted Domain Extension).
But as we are seeing workloads being more and more heterogenous, having to work on GPS and accelerators becomes habitual.
VM (Virtual Machine)
VM or a virtual machine is a logical construct that is created by a thin layer of software called a hypervisor, which allows user-level software applications running in this environment to believe that it has its system all to itself.
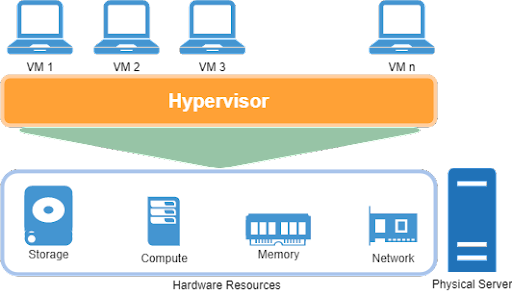 A virtual machine allows multiple machines essentially to be running at the same time so we get more utilization of CPU which is a resource we care about, and get maximum utilization out of it.
A virtual machine allows multiple machines essentially to be running at the same time so we get more utilization of CPU which is a resource we care about, and get maximum utilization out of it.
This was pretty transformational in cloud service providers, where instead of having a dedicated server for each enterprise now it could be dedicated to multiple enterprises.
Virtualization History
- Until the early 2000s, virtualization technologies had been an exclusive domain of the mainframe.
- IBM arguably invented virtualization in the 1960s, and it was pretty much widely used in the mainframe context. But for commodity hardware to x86, sun spark and all those nice processors it was just an operating system and applications.
- It wasn't until companies like VMware came along and proved the efficiency of virtualization on commodity hardware.
- And that preceded the boom of cloud computing because it allowed the cloud providers and large data center providers to provide this capability at really great efficiency.
What is TDX?
Known as Trust Domain Extensions. Essentially all it does is take the VM abstraction and embrace it and say that's the Trusted Execution Environment.
Initially creating some confidential VMs and calling them trust domains and hence trust domain extensions.
So these trust domains are confidential VMs which are computing environments that TDX supports.
Trust Domains
These are VM onto themselves but the boundary of the VM, which has been in the past an OS, a bunch of memories, and some applications, that boundary is now the Trusted Execution Environment. The thing that is protected.
So for a trusted domain: we are essentially taking a VM and we protect the content of the whole thing (the OS, the applications, and everything that is under the VM become protected or a trusted domain).
TDX vs SGX
TDX: It allows you to take an entire VM. Many people just want to take the entire application because it is a legacy code and can't be refactored. So plopping that into a secure VM. That's why we're seeing a lot of interest in these VM-based confidential computing technologies.
SGX: It allows one to write an application and then decide which pieces of that application we want to separate and secure. It then protects that part only.
Use Cases
Both of these new technologies are equally helpful but it depends on what your use cases are. Some of them might be the following:
If you're writing some software from scratch, that never existed before and you care about security. You may want to use a technology like SGX because that allows you to focus on just the pieces you care about.
But if you have a bunch of legacy software and have been in business for over 40 years and you have tons of legacy software. don't even know where the source code is. Then you want to run it in a VM. Something like TDX is good enough for them.
Hope you enjoyed this discussion on some hot technologies. Feel free to comment down your queries about Confidential Computing 🚀.
